6. NEBTC Network
NEBTC Network, designed to be automated and decentralized, runs on a blockchain protocol fully and autonomously in accordance with rules encoded via smart contracts (DAO Governance). D.Volt platform is operated on NEBTC Network, which is governed by DAO (Decentralized Autonomous Organization).
6.1 DAO Governance
A DAO, a decentralized autonomous organization, is a software-enabled organization built and governed by smart contracts on a blockchain network. A smart contract is a set of rules written in computer code on a blockchain network that enables a network of computers to communicate and execute pre-programmed transactions once certain conditions are met. A DAO does not have a CEO or a board. It is owned by the members (nodes) and make decisions based on proposals that nodes vote on.
A DAO has received much attention because it offers many advantages such as transparency, no corruption or owner risk, equitable distribution of earnings, etc.
6.2 Consensus Algorithm; PoA-NP (Proof of Authority-Node Pool)
NEBTC Network uses Proof of Authority-Node Pool (PoA-NP). PoA-NP is a community-based consensus algorithm that introduces a practical and efficient solution for blockchain networks.
A node pool is a community of nodes who own a Vein-X NFT which can be obtained by purchasing a D.Volt package designed to airdrop NEBTC coins. NEBTC coins airdropped is locked lifelong but used only to form an x node. Anyone who receives NEBTC airdrop deserves to run an x node. An x node is a fundamental unit that comprises a node pool. X node holders can delegate to node pools if they wish to participate in the protocol and receive rewards.
There are two ways an x node holder can earn rewards: by delegating their x node to a node pool run by someone else, or by running their own node pool.
The number of x nodes delegated to a certain node pool is the primary way the NEBTC Network protocol chooses who should add the next block to the blockchain and receive a monetary reward for doing so. The more x node is delegated to a node pool, the more likely it is to make the next block – and the rewards that it earns are shared between everyone who delegated their x node to that node pool.
Node pools are run by a reliable operator with the knowledge and resources to run the node on a constant basis.
In NEBTC Network, transactions and blocks are validated by selected node pool operators, called validators. Selected node pool operators run software allowing them to put transactions in blocks. The process is automated and does not require node pool operators to be constantly monitoring their computers. It, however, does require maintaining the computer uncompromised.
Individuals qualified for an x node earn the right to become node pool operators.
New node pool operators acting as a validator can be selected in accordance with the size of the node pool they generate.
Selected node pool operators(validators) take turns signing and creating blocks at a set period.
The first selected node pool operator must be registered in the Genesis Block.
Selected node pool operators can be removed through voting among operators.
PoA-NP of NEBTC Network delivers comparatively fast transactions.
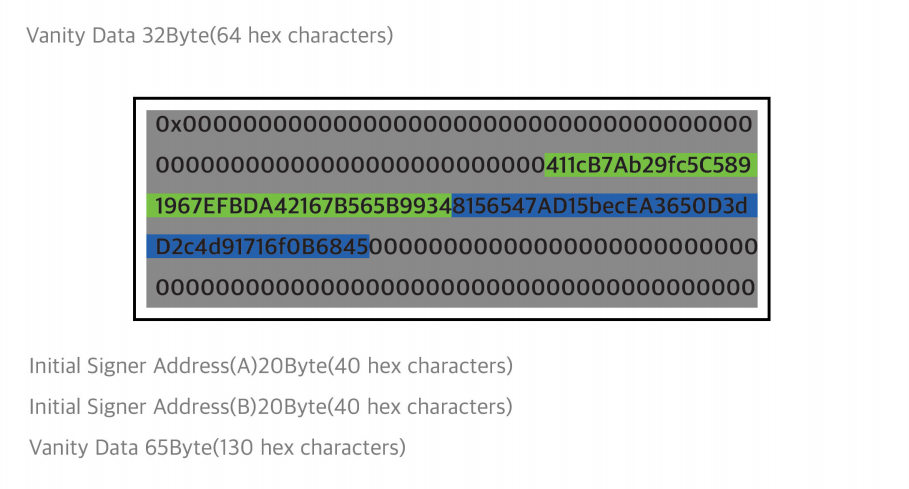
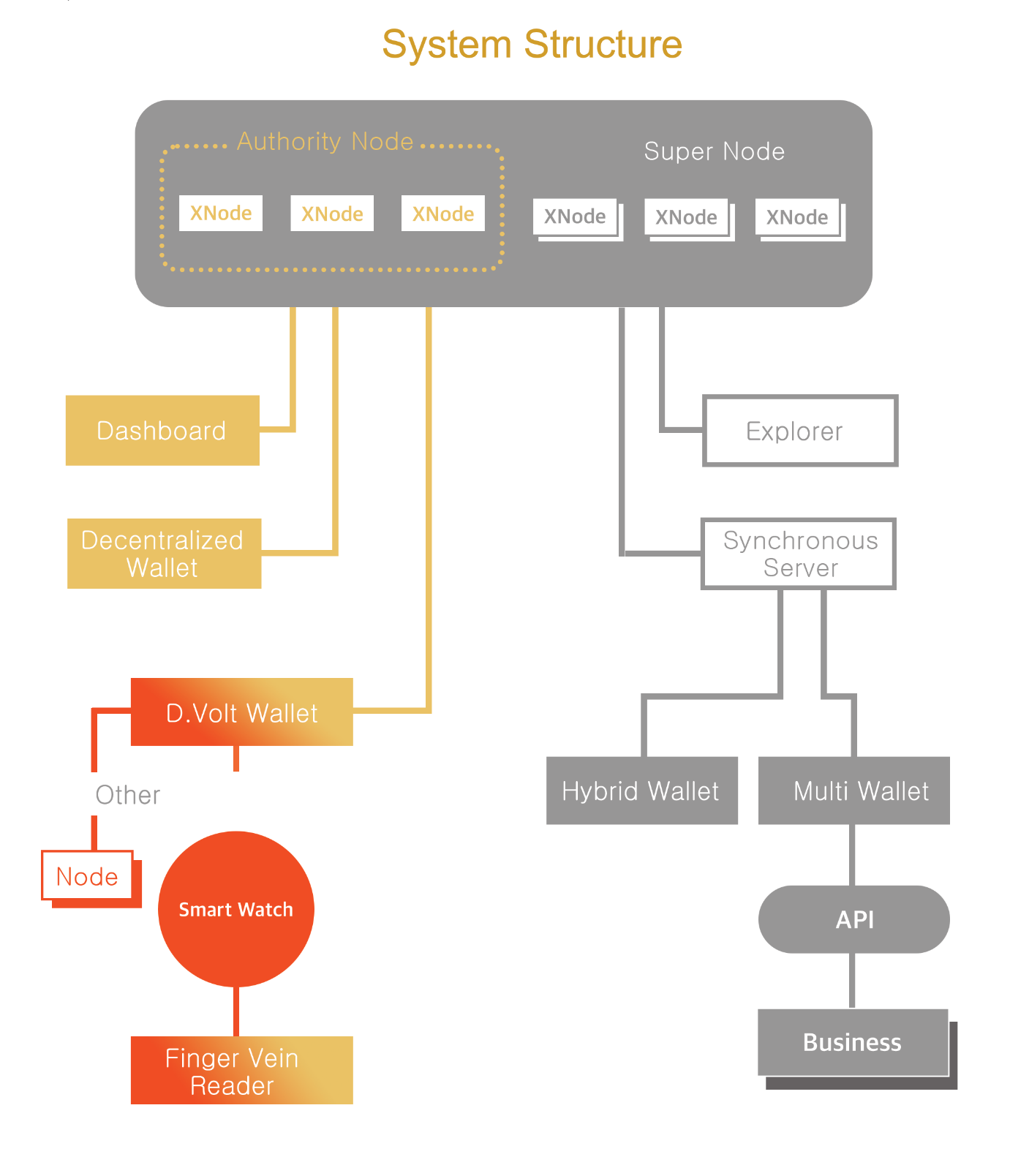
6.3 A Major Role of a D.Volt package in NEBTC Network
A D.Volt package is composed of a finger vein reader, a D.Volt wallet, and a smart watch. It has been developed for the purpose of setting up nodes in the NEBTC Network. Each D.Volt package is NFTized and provides a D.Volt NFT as a certificate of authenticity. Each D.Volt package contains its own information such as its model name and the number of NEBTC airdrop coins given. Whoever wants to run a node should have a D.Volt NFT. Airdrop coins are used only to set up a node. Anyone with NEBTC airdrop coins is eligible to run a node.
6.4 Nodes in NEBTC Network
A blockchain consists of numerous blocks of data. These blocks of data are stored on nodes that can be compared to small servers. On a blockchain, all the nodes are connected to each other and they continuously exchange the newest information on the blockchain with each other. This ensures all nodes are updated.
In NEBTC Network, there are three kinds of nodes; x-nodes, super nodes and authority nodes.
An x-node is a fundamental part of NEBTC Network blockchain network. Only x-nodes are eligible to build a node pool, a community that is composed of not less than three x-nodes.
There is no limit to the number of node pools, but a total number of super nodes and authority nodes is initially set at a minimum of 100 for the stability of the blockchain network. If needed, the number of super nodes can be increased (or decreased) by voting.
The total number of x-nodes in a node pool can serve as a criterion for selecting validators. According to the size of the node pool, super nodes and authority nodes are determined; Node pools from 1st to 5th are called authority nodes, and 6th to 100th super nodes.
6.4.1 X-node
X-nodes receive rewards in return for a service, such as either participating in an existing node pool or newly building their own node pool. An x-node should be in a node pool to receive x-node rewards.
6.4.2 Super node
Super nodes communicate with the blockchain while relying on authority nodes to provide them with the necessary information. They store a copy of the blockchain, and broadcast transactions for processing.
Super nodes receive additional rewards in return for a service, such as storing and communicating with the blockchain.
6.4.3 Authority Node
Authority nodes act as a server in NEBTC Network. Their main tasks include maintaining the consensus between other nodes and verification of transactions. They also store a copy of the blockchain, thus being more secure and enable custom functions such as instant transfers and private transactions.
When making decisions for the future of a network, authority nodes are the ones that vote on proposals.
Authority nodes receive additional rewards in return for a service, such as verifying transactions, broadcasting transactions, storing a copy of the blockchain, and so on.
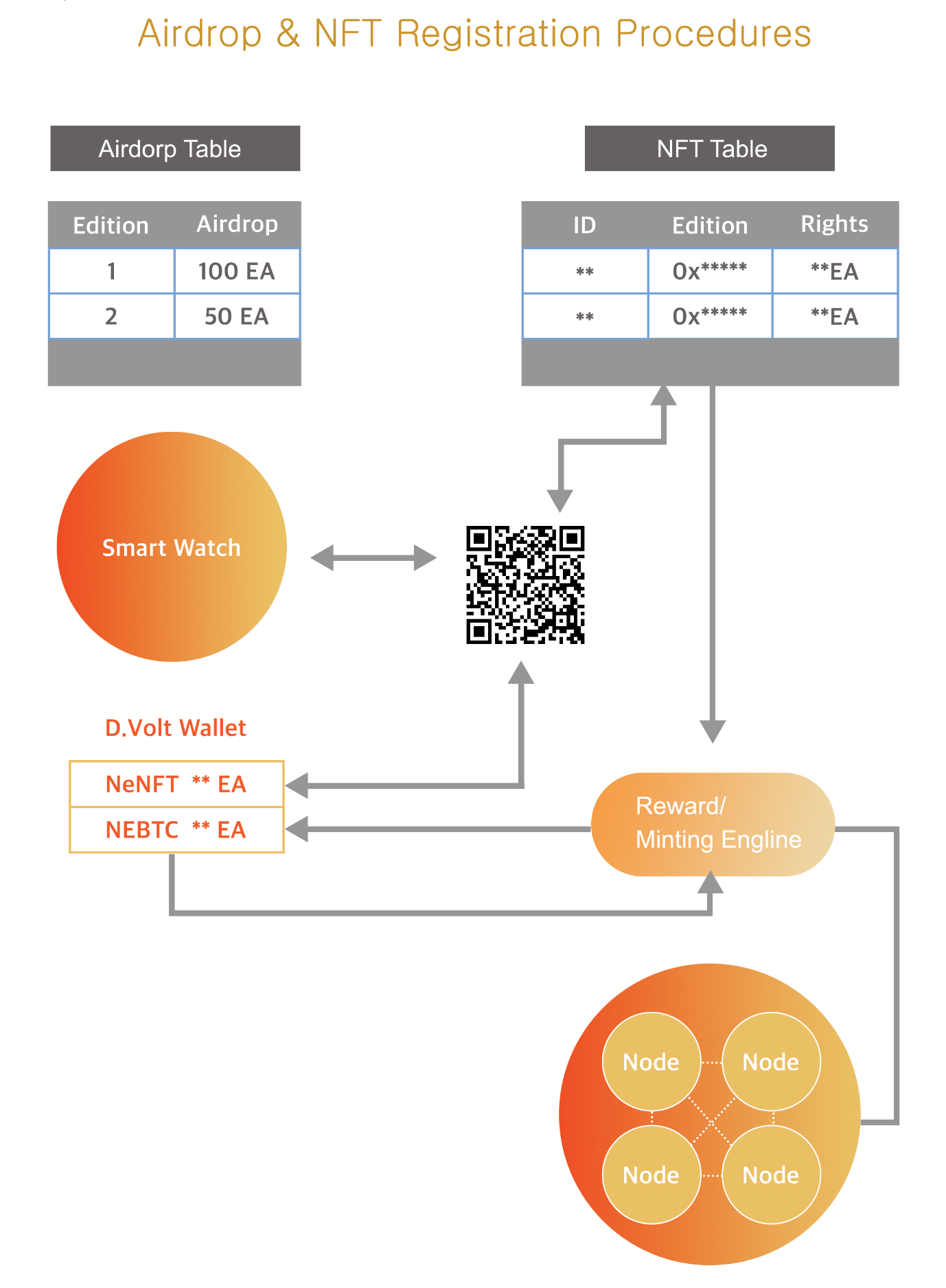
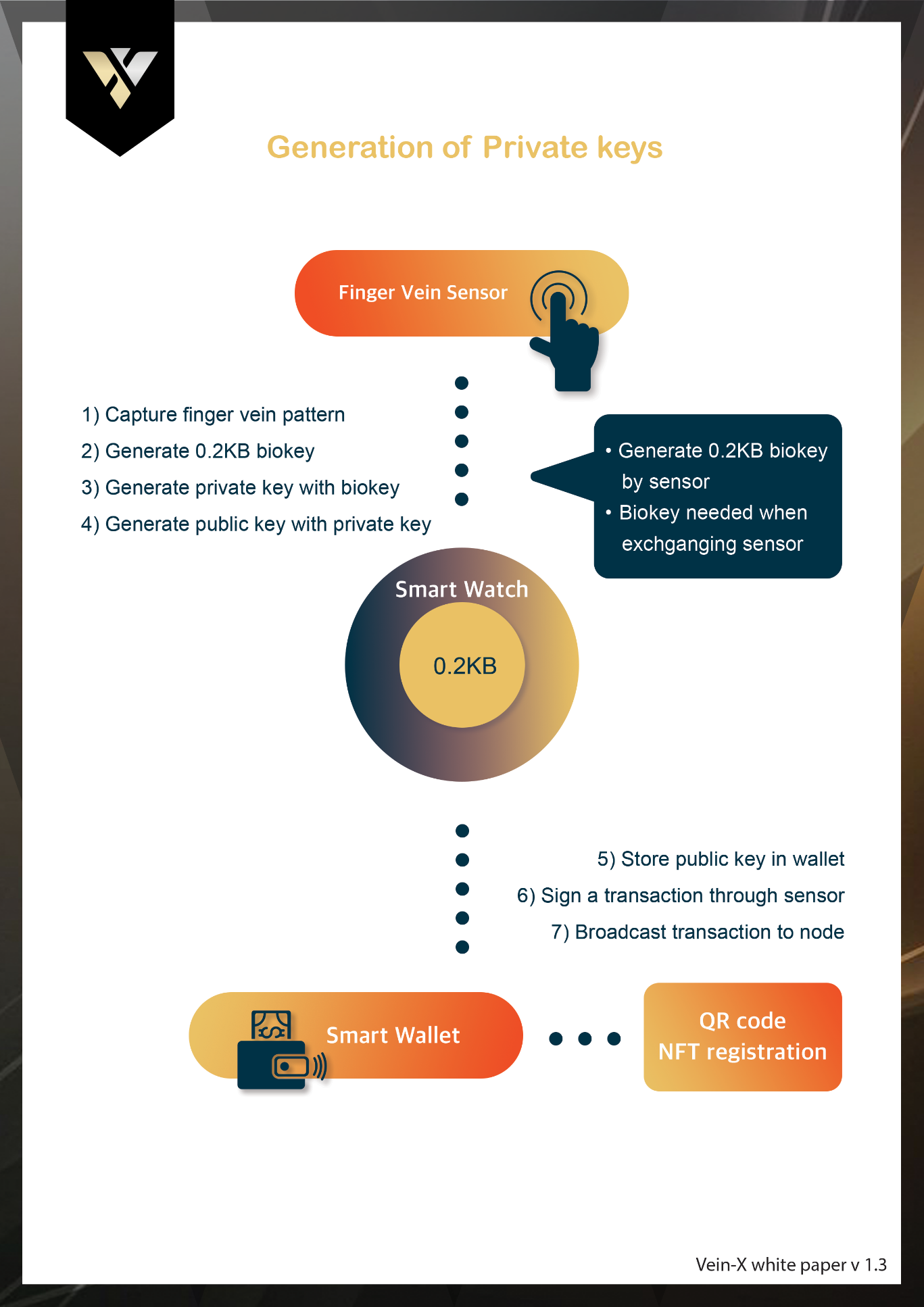
Airdrop & NFT Registration Procedures


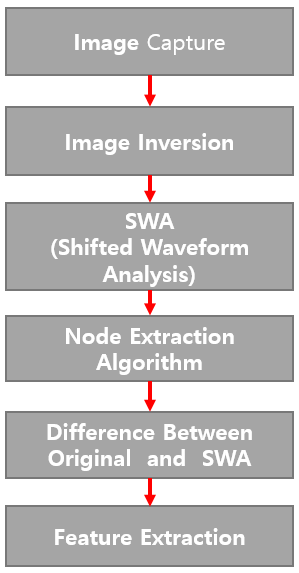
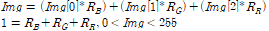

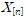 is shifted by d to get
is shifted by d to get 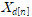 . δn is obtained by calculating the difference between
. δn is obtained by calculating the difference between 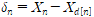 ).
).